I love this time of year. Whilst most people are thinking about summer holidays and time off work, instead I’m eagerly anticipating the result from the Sophos State of Ransomware Report for 2023. Perhaps I’m a little unusual in that regard, but nevertheless the report is a veritable treasure-trove of information that gives us a unique perspective on the current cybersecurity landscape and glimpse into the murky underworld of the cybercriminal. If you aren’t familiar with the report, you might be wondering what the format is and what the statistics tell us. If you’re interested, you’re invited to read on.
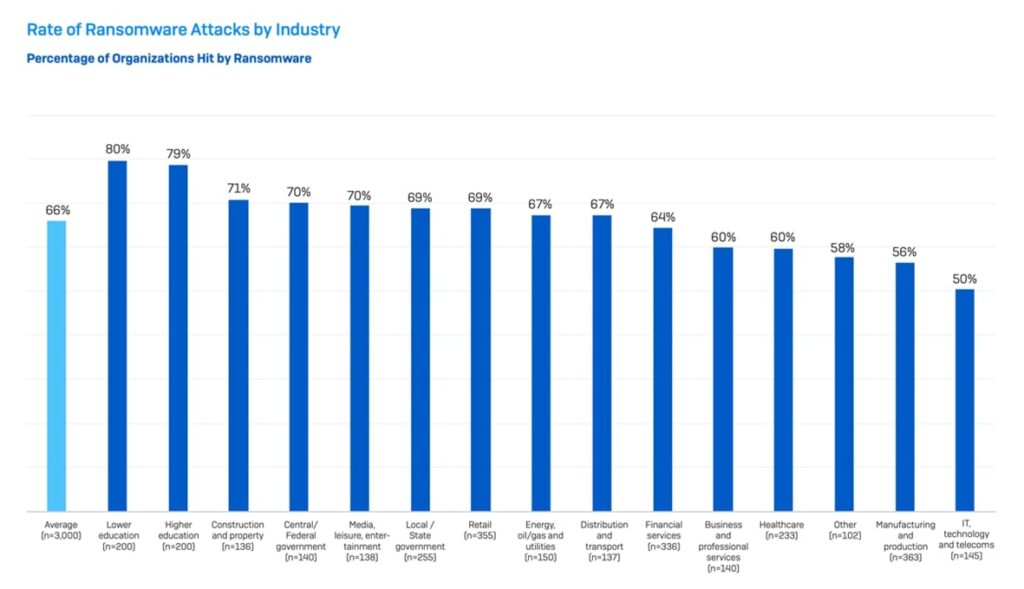
Let’s begin with the headline statistic – of the 3,000 organisations worldwide that were randomly selected and participated this year, 66% of them experienced at least one ransomware incident in the 12 months preceding the survey. Allow that to settle in, two in three organisations had ransomware, as if that number wasn’t shocking enough, it’s a mirror of the results last year that tell us, perhaps unsurprisingly, that ransomware is, and continues to be a significant challenge for organisations across the globe. What is also rather concerning is that of those attacks, in 76% of cases, the criminals managed to encrypt at least some of the target data. I should probably emphasise at this point, that the respondents were selected at random and are most likely not current Sophos customers. Needless to say, this tells us that the security measures and ransomware protection these organisations were pinning their hopes on have sadly let them down. The final two stats (for now) are that 46% of the victims elected to pay the ransom and place their faith in the honesty of crooks and that the average cost of a ransomware incident is now an eye-watering $1.82 million.
Thanks to the very public disagreement within the Conti ransomware group with regards to their cyber-support of the Russian invasion of Ukraine and the subsequent data leaks we already know that the criminal gangs are highly organised and structured groups that are a far cry from the images the media images that portray hoodie-toting teenagers hiding out in their mother’s basement. It is clear that these groups have a wealth of resources, both fiscal and human and that these are deployed tactically to maximum effect. One of the interesting insights that the State of Ransomware Report gives us, is who the cybercriminals target, and from that we can infer a lot about their motivations and methodologies. Not all sectors suffer equally, and those that are hit hardest are perceived by the cybercriminals to be the softest targets and / or the most likely to pay. Conversely, the sectors that are seen to be more strongly defended or exhibit a lower propensity to pay are typically avoid the attentions of the criminal gangs, after all, in the main, the groups are motivated by return on investment decisions that are not dissimilar to the processes a legitimate business would go through.
To illustrate the variances and disparities that exist, the sectors that experience the most incidents of ransomware are the upper and lower education sectors, 80% of respondents in these sectors experienced a ransomware incident. At the opposite end of the spectrum, 50% of the respondents in the communications and high technology sectors had a similar incident. The fact that high technology invests the most in cybersecurity whilst education is typically under-funded goes a long way to explaining the disparity. Interestingly, organisation size when expressed by head count has little to no correlation with the likelihood of attack, but an organisation’s turnover has a distinct link.
A common question that inevitably comes up whenever I discuss these statistics is ‘how much will the bad guys demand and should I pay them?’. In a somewhat cynical manner, the cybercriminals will already have worked out exactly what their victim’s ability to pay is and will target their ransom accordingly. Setting a demand that’s too high will turn a victim away, conversely, they do not want to leave money on the table with a demand that is too low, its something the criminals have down to a fine art. Should you pay – well that’s not an easy question to answer. Of course, in an ideal world you shouldn’t pay the ransom demand, after all you are effectively perpetuating the problem by encouraging the trade. Victims often don’t get a fair deal by paying, there are some outlying groups who have no intention of restoring aces to your data, whereas other gangs might want to try, but their decryption tools are not fully tested. These decisions are perhaps a little less clear cut when we move from the theoretical to the reality of a hospital in which doctors cannot access patient records or a factory that is idle due to the corruption of data. What is certain is that paying up isn’t a quick win, with organisations who elect to pay typically experiencing longer recovery times and as much as double the overall cost of an incident when compared to restoring from a back up.
Analysis of this data within the State of Ransomware is an interesting academic exercise in its own right, but there is much we can learn that can be turned into practical ways to better defend ourselves.
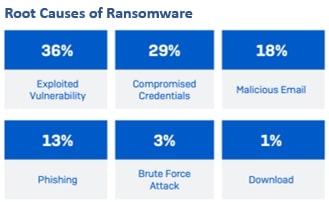
The first thing we can glean is that email is a popular attack route for the criminals which encompasses about 30% of attacks with a little rounding. Essentially as we get better at defending our estates technically, social engineering is becoming an increasingly important part of the cybercriminal arsenal. Much can be done in educating users in spotting phishing attacks and also not oversharing data online that can, and is, exploited by the gangs to create ever more timely and compelling phishing campaigns.
The other elements are more technology-based problems, for example using compromised credentials or exploiting a vulnerable system. Although there are technical mitigations exist in some scenarios, this too is, at its heart a human problem. Cybercrime tactics continue to evolve and a common approach is to utilise existing and legitimate software with in victim’s environment in a technique known euphemistically as ‘living off the land’. Intrusions of this nature are incredibly hard for technology alone to combat and often renders endpoint protection trapped in an ineffectual cycle of being unable to determine if the actions are those of a legitimate administrator or nefarious third party. In essence, the tech lacks the ability to apply context and intuition to these events, in a way that is second nature to skilled human threat hunters. The solution is to employ these experts to investigate suspicious events and respond according when the need arises.
Cybercriminals have become much more coordinated and act collaboratively to meet their goals. Perhaps the greatest defence that we have is to also similarly pool resources using Managed Detection and Response services to concentrate threat hunting skills and deliver better cybersecurity outcomes to all users by learning from one incident and applying that knowledge to all subscribers. At Sophos we have built a sophisticated process so that when an investigation is conducted in one organisation, the findings become baked into our protection solutions within mere minutes, even when that telemetry may have come from another vendor’s cybersecurity product.
The cybercrime war will continue to rage on, and our best hope is to work collectively within the MDR framework, to ensure that there are more of us doing good things than there are bad actors intent on harm.

Jon will be speaking in more detail about the State of Ransomware 2023 report at our online Optimise event on 19th September. Jon will also be on hand to answer any of your questions after the webinar.
Register for your place at this and one of our other webinars from our cyber security partners here.

